When shopping for a healthcare CRM, you may have encountered software described as HIPAA-compliant. You would infer that HIPAA is a law, and you'd be correct. It stands for the Health Insurance Portability and Accountability Act, passed by Congress and signed into law in 1996; among other thing, HIPAA governs the privacy and security of patient data handled by healthcare providers or related entities.
HIPAA was written in response to the adoption of new technologies in the healthcare industry. In the 90s, with the widespread use of computers and electronic transmission of information, it became essential to develop and enforce standards to maintain patient confidentiality. HIPAA aimed to establish those standards, and with civil and criminal penalties facing those who failed compliance audits, HIPAA-compliant policies, practices and protocols became essential. This also applied to the software used by medical institutions. HIPAA-compliance is widely expected for software used in the healthcare industry, which is why there is a subset (or analog, depending on your perspective) of the CRM industry called Patient Relationship Management.
This term refers to CRM software tailored for healthcare use. For ease of reference, this article will call such software healthcare CRMs, or healthcare helpdesks, as the case may be. Healthcare CRMs and healthcare helpdesks are HIPAA certified as a matter of necessity, and they are one tool to ensure healthcare-relateed entities minimize their chance of a breach of confidential data and thus avoid incurring civil penalties.
So what exactly is HIPAA? And how does it relate to CRM? Let's read on.
What is HIPAA?
As mentioned, HIPAA was a law passed in 1996 to standardize policies, guidelines, and protocols governing the introduction and use of digital technology in the healthcare industry. There are sections, or Titles, to the law:
Title I: Health Care Access, Portability and Renewability
Title II: Preventing Health Care Fraud and Abuse; Administrative Simplification; Medical Liability Reform
Title III: Tax-Related Health Provisions Governing Medical Savings Accounts
TItle IV: Application and Enforcement of Group Health Insurance Requirements
Title V: Revenue Offset Governing Tax Deductions for Employers
Of these sections, Title II pertains most to software used by healthcare providers. It governs the electronic use and dissemination of confidential patient data. Title II is most relevant to healthcare CRMs and healthcare helpdesks; when such software is described as HIPAA-compliant, it suggests the security architecture and practices of the platform and the vendor meet the standards required by HIPAA Title II. This section was modified with the passage of the HITECH Act of 2009 -- more on that soon.
How exactly does HIPAA/HITECH affect healthcare CRMs?
HIPAA Title II defines policies, guidelines, and procedures for maintaining the confidentiality and security of patients’ personal and medical information as well as civil and criminal penalties for noncompliance. The law also created Administrative Simplification rules -- or industry standards intended to streamline compliance and enforcement -- that applied to “covered entities” as defined by HIPAA and the Department of Health and Human Services. These covered entities refer to healthcare plans, healthcare clearinghouses, and healthcare providers that interact with patient data in analog or electronic formats. The latter, of course, applies to software used by covered entities, such as healthcare CRMs and healthcare helpdesks.
Title II of HIPAA established five Administrative Simplification rules: the Privacy Rule, the Transactions and Code Sets Rule, the Security Rule, the Unique Identifiers Rule, and the Enforcement Rule.
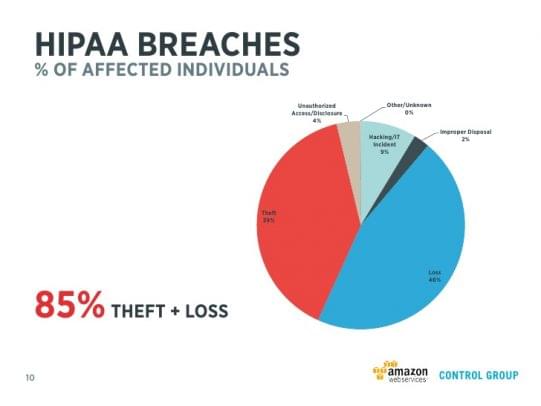
Privacy Rule -- The HIPAA Privacy Rule regulates the use of disclosure of Protected Health Information (PHI), which is any information about health status, provision of healthcare, or healthcare payments as used by the covered entities. These entities may disclose such information in limited cases as required by law, such as for missing persons or suspected child abuse. Covered entities typically interpret the Privacy Rule to cover all parts of a patient’s medical record or payment history, as rule violations can incur civil or criminal penalties as well as steep fines. A corollary of the Privacy Rule, often cited as its own rule, is the Breach Notification Rule in which covered entities are required to notify affected parties in the event of unauthorized disclosure, leak, or loss of Protected Health Information.
In 2013, HIPAA was updated via the Final Omnibus rule that implemented provisions of the Health Insurance Technology for Economic and Clinical Health (HITECH) Act that expanded the privacy and security requirements from covered entities to include their business associates. HITECH also updated the Breach Notification Rule. This meant that so covered entities were required to report the event of a breach of Protected Health Information, unlesss it could be demonstrated that affected parties hadn't experienced “significant harm"; previously, covered entities were given the benefit of the doubt.
Transactions and Code Sets Rule -- This rule intended to standardize classification of medical encounters, procedures, and transactions for covered entities governed by HIPAA. Healthcare providers filing for reimbursement from the Center for Medicare and Medicaid Services (CMS) must file claims using the correct code to qualify for reimbursement.
Security Rule -- The Security Rule complements the Privacy Rule. The Privacy Rule pertains to all Protected Health Information, written or electronic, while the Security Rule pertains exclusively to PHI distributed over electronic channels. It lays out three types of safeguards -- administrative, physical and technical -- that covered entities must establish in order to comply with HIPAA.
- Administrative safeguards refer to the internal policies and procedures to maintain oversight of the privacy and security of patient data according to HIPAA standards. This includes policies determining which types of employees have access, how management maintains oversight, the characteristics of internal audits, the provision of adequate training to ensure proper data handling, and so forth.
- Physical safeguards refer to the physical access to the data. This includes a secure location for hardware and software within the premises, policies limiting access and visibility only to authorized individuals, proper disposal of retired equipment to prevent compromised data, etc.
- Technical safeguards refer to the protection of electronic storage and communication of data. This refers to the encryption of information transmitted over open networks, ensuring data has not been deleted or changed, authenticating data integrity and the identities of individuals to whom data is sent, a written record of all configuration settings on network components, documented risk analysis and risk management programs, as well as data backups and disaster recovery protocols.
Unique Identifiers Rule -- This simply applies a unique 10-digit National Provider Identifier (NPI) for covered entities under HIPAA to facilitate standard transactions between healthcare providers, clearinghouses, large health plans, and various government agencies. Covered entities would receive a single 10-digit code for identification, although some large institutions might receive multiple NPIs for discrete facilities, such as cancer centers or rehab facilities.
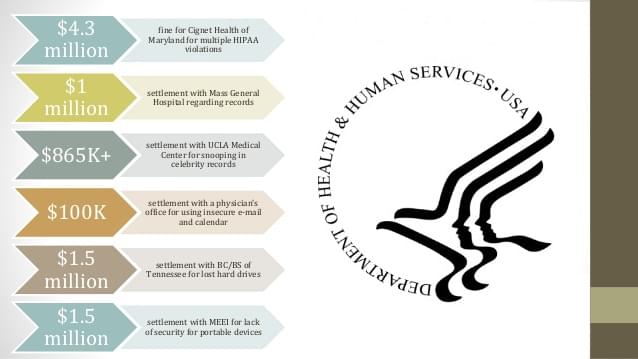
Enforcement Rule -- The Enforcement Rule established civil monetary penalties for noncompliance with HIPAA, which became effective in 2006. According to the Department of Health and Human Services, the most frequent issues of noncompliance were, in order: misuse and disclosures of PHI, lack of protection of health information, patients unable to access their health information, disclosure of more than the necessary minimum PHI, and a lack of safeguards of electronic PHI.
The covered entities most commonly required to take corrective action to remain in compliance with HIPAA were, in order, private practices, hospitals, outpatient facilities, group plans (insurers), and pharmacies.
Such covered entities, when shopping for patient relationship management software such as a healthcare CRM or a healthcare helpdesk would be most interested in whether the software satisfies the first and third of the Administrative Simplification rules; in other words, the Privacy Rule and Security Rule. Failure to properly ensure the confidentiality and security of their patients’ data could result in significant loss for the covered entity; by extension, healthcare-oriented software solutions would be on the hook themselves if they advertised HIPAA-compliance yet failed to meet the standards.
How do healthcare CRMs and healthcare helpdesks become CRM HIPAA Compliant?
Software that handles Protected Health Information needs to account for the Administrative Simplification rules in HIPAA Title II, particularly the Privacy Rule (as modified by HITECH) and the Security Rule. The Security Rule outlines administrative, physical, and technical safeguards required for compliance. Software developers naturally focus first on the technical safeguard standards, but vendors whose solutions are offered over the cloud will also account for the physical security of their servers and the administrative policies determining who can access them and when.

The Security Rule intends to protect confidential medical data while allowing healthcare providers the flexibility and scalability to incorporate new technologies into their practice. To be CRM HIPAA compliant, there are four general responsibilities outlined by the Security Rule that state covered entities must:
1. Ensure the confidentiality, integrity, and availability of all e-PHI they create, receive, maintain or transmit.
2. Identify and protect against reasonably anticipated threats to the security or integrity of the information.
3. Protect against reasonably anticipated, impermissible uses or disclosures.
4. Ensure compliance by their workforce.
The Department of Health and Human Services goes into more detail on a page dedicated to summarizing the Security Rule.
Software vendors striving to meet government security standards are usually transparent on the lengths to which they secure their data centers, networks, applications, and any additional security protocols. If their software is offered over the cloud -- as many healthcare CRMs or helpdesks are -- vendors can match their premises to industry auditing or security specifications to ensure security of their servers including redundancy for power.
Vendors can provide additional on-site security with surveillance, security guards, a secured facility with visitor authentication and alarm systems. Some vendors provide customers a choice in which region they prefer their data to be stored.
Vendors can protect their networks with secure HTTPS transport, regular audits, network intrusion detection technologies, redundant firewalls and a dedicated, responsive security team. Regular network security scanning protocols can offer insight for potential vulnerabilities. And if you send a lot of documents, it's worth investing in a secure HIPAA compliant eFax solution.
HIPAA Title II Security Rule compliance, unlike other security certifications, isn’t officially recognized by a governing body. Private companies that claim HIPAA compliance are explicitly not endorsed by the HHS. (This stands in contrast to Payment Card Industry (PCI) Data Security Standard compliance which is validated by external assessors according to standards made by an industry council.) Therefore, covered entities -- healthcare providers, clearinghouses and plans -- using HIPAA ‘certified’ software do not absolve themselves of responsibility in the event of a security lapse.
A covered entity could feel more confident if a vendor whose software would handle Protected Health Information were willing to sign a Business Associate Agreement (BAA), which would extend to them responsibility for the privacy and security of PHI as determined by the HITECH Act. Willingness to sign a BAA could be construed as a sign of vendor confidence in their security architecture, policies and procedures.
All this for a healthcare CRM?
All this, yes. HIPAA/HITECH takes very seriously the proper handling of patient data. Covered entities face significant penalties for failing to ensure the privacy and security of patient data, so patient relationship management solutions, like healthcare CRMs or helpdesks, which offer the highest level of security will be the most attractive options.
Looking for a HIPAA-compliant CRM or helpdesk? Compare options in our free comparison guides for CRM software and online ticketing solutions.



