A great deal of responsibility falls on companies asking for customer data. Such a request is usually made under the auspice of improving services -- which is a reasonable proposition if you’re a customer -- and there should be a reasonable expectation that the customers’ data will be protected. After all, making data available to one commercial entity -- as partial exchange for improved services to-be-rendered -- hardly means it's available to simply anyone at the company, let alone a curious outsider.
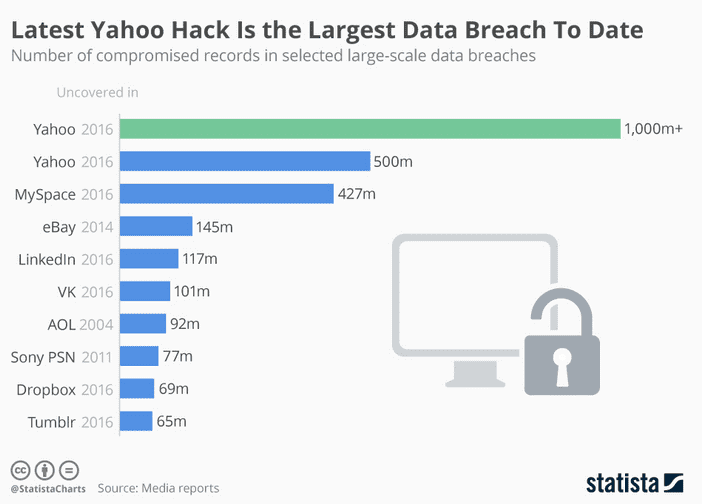
But losing customer data, whether through accidental exposure or a data breach, isn’t merely a matter of customer trust. Your customer data is also a commercial asset (and your ability to protect it a reputational asset). Yahoo’s disclosure of the 2013 and 2014 data breaches that compromised the personal data of 1.5 billion users -- their names, email addresses, phone numbers, and dates of birth included -- caused their sale price to Verizon to tumble by $350 million. It is the largest data breach to date.
Of course, vulnerabilities exploited against companies transfer vulnerability to the customers who trusted them. Companies that rely on customers’ trust for absolute privacy (*cough* Ashley Madison) will find their reputations irrevocably tarnished.
Suffice to say, companies have plenty of reasons to secure their customers’ data: it affirms their trust and ultimately protects their loyalty, your reputation, and your bottom line.
Data Security in a CRM
The deployment of customer relationship management systems has traditionally closely followed technological norms. CRM systems were operated through on-premises databases throughout the 80s and 90s (the era of its birth). However, since the turn of the century, CRM solutions have been following an approach largely pioneered by current industry behemoth Salesforce: deploying through cloud-based servers as Software-as-a-Service (SaaS). The switch to SaaS is picking up speed; many enterprises retain on-premises deployments, but Gartner predicts that 10% of $1 billion-plus organizations will run all their CRM applications on SaaS.

Companies that use on-premises CRM systems have additional security concerns compared to companies that use SaaS CRM solutions -- primarily ensuring physical security -- but regardless, both types require preventive measures to ensure security of the local network.
Securing Your Servers and Your Network
On-premises CRM solutions offer companies more control over deployment, security, maintenance, upgrades, and support. But increased control does not, by default, make the system more secure. It gives the company increased flexibility to implement and adapt software to internal needs, but also increased responsibility to secure and protect physical, local, and remote access. Never forget to take help from Virtual Private Network in the whole scenario to get better results.
Securing Physical Access to Your ServerThe term ‘server’ can describe your server software or the physical computer in which the software and your company data reside. Regarding this level of security, the latter definition applies. Physical access is the easiest way for unauthorized individuals to remove data from your servers; fortunately, it also entails the most straightforward safeguards.
- Isolate your servers in a specialized area. Server rooms are specialized for the continuous running of computers, with climate control, fire protection, future proofing (to accommodate future growth and more servers), and power supply redundancies. Establish rules for any personnel inside the server room -- restrict smoking, food and beverages, keep the door shut, and limit the number of personnel permitted inside at any given time.
- Ensure all power sources to the server room are secured. If your patch panel must be located in another room, ensure that room is secured as well. The same goes for any redundancies located outside the server room.
- Restrict access to the server room. Some companies save space by doubling their server room as a storage room, office, or other usable space. Don’t do this. Restrict access with a lock -- keyed, electronic, access control card -- and designate a full-time employee to delegate and monitor access according to security protocols (specific credentials, certain lengths of time, with or without supervision, etc).
Local ‘insider’ threats and remote attacks are far more common than someone infiltrating your office and personally removing data from your physical server. Server access through the local network and remote intrusions are responsible for the majority of data breaches; therefore, encrypting network transactions and securing digital access are major components for both on-premises and SaaS CRM systems to ensure server security.
Your local network consists of the computers in your office, which are connected through a router. Local networks don’t need to be connected to the internet, but as most businesses are, this article assumes the same for your company.
There are several precautions you can take to protect your local network from attacks that would disrupt your business.
- Change the SSID of your router. Don’t use the name of your business; use an innocuous name or code that deflects attention from unwanted visitors attempting to gain a wifi connection.
- Disable your router’s SSID broadcast. Disabling the SSID broadcast on your router prevents devices detecting your wireless network when viewing available networks in the area. This can deter the occasional, unwanted visitor attempting to log into your network.
- Create strong admin login credentials. Ensure unauthorized users cannot easily guess or brute force their way into your router administrator panel. A strong password is at least 8 character long, consists of both uppercase and lowercase letters, includes digits and punctuation marks, and isn’t based on personal information or a dictionary word. Don't use the default router password; it’s also good practice to periodically update your password.
- Disable remote management for the router. Your router’s management interface most likely does not need to be available via the internet. Disabling web-based management restricts access to your local network. If remote access is required sometimes, consider using a virtual private network (VPN) for added security.
- Ensure your browsers are updated to support HSTS. HSTS, or HTTP Strict Transport Security, is a web security policy that ensures transactions between your router and local devices are encrypted. HSTS limits the effectiveness of eavesdropping and DNS spoofing. For local networks connected to the internet, this means that malicious actors with access to your local network (with a WiFi password, for example) would have a harder time successfully targeting local devices.
- Enable a firewall for computers on your network. Firewalls come in two types -- hardware and software. Both can restrict access to and from certain IPs (whitelisting and blacklisting) and disable certain scripts. Some routers come with a hardware firewall built in; others you can connect separately. Software firewalls are installed in separate instances on individual computers (and are often bundled with antivirus and antispam software). Small businesses can benefit from a software firewall, in which each team member configures it to their needs. A hardware firewall is best for a larger company seeking to restrict or enable access on a department-wide level.
Precautionary measures and effective router management will be able to prevent most attacks, from eavesdropping, DNS spoofing, denial-of-service attacks to the execution of malicious code and man-in-the-middle attacks. As access to your CRM data will come through the local network, securing your network is critical to ensuring CRM data security.
Looking for a SaaS CRM solution? Check out our comparison guide on sales force automation.